In the realm of runtime security monitoring, invisibility becomes the greatest weapon in the ever-evolving battle against cyber threats. In a digital landscape fraught with sophisticated attacks and stealthy adversaries, traditional static security measures are no longer enough to safeguard our systems and data. The need of the hour is real-time visibility into our applications and infrastructures, allowing us to uncover malicious activities as they happen and respond swiftly to mitigate potential damage. In this blog post, we will delve into the captivating world of runtime security monitoring, exploring its significance, benefits, and presenting the Runtime Security Monitoring tool, the answer of PIACERE technology in pair with innovative technologies that can empower us to stay one step ahead of the lurking shadows.

PIACERE’s runtime security monitoring tool ensures that the conditions of the QoS are always met and that a failure or non-compliance of NFRs is not likely to occur, with verified security violations at runtime. It is addressing the need for monitoring stack for the run-time conditions so that the self- learning and self-healing mechanisms can be fed. It does so through a monitoring system capable of detecting security-related events and incidents in the deployed application’s environment. It is (to the extent possible) deployable automatically and notifies users about security alerts.
In complex systems, verification is not only a matter concerning the pre-operation steps, but it also encompasses the operation of the system. In particular, it is of paramount importance to make sure that the system undergoes through a continuous runtime verification for what concerns any security violation. Such violations can be recognized by monitoring of various security metrics (e.g., file integrity, network configuration changes, usage of software reported as vulnerable, malware detection) and integration with the monitoring component to recognize violations of defined security policies and alert DevSecOps teams to address and eliminate threats as fast as possible. Through security verification and threat detection on multiple levels, the PIACERE framework empowers deployed applications by helping to prevent abuse and leakage of data.
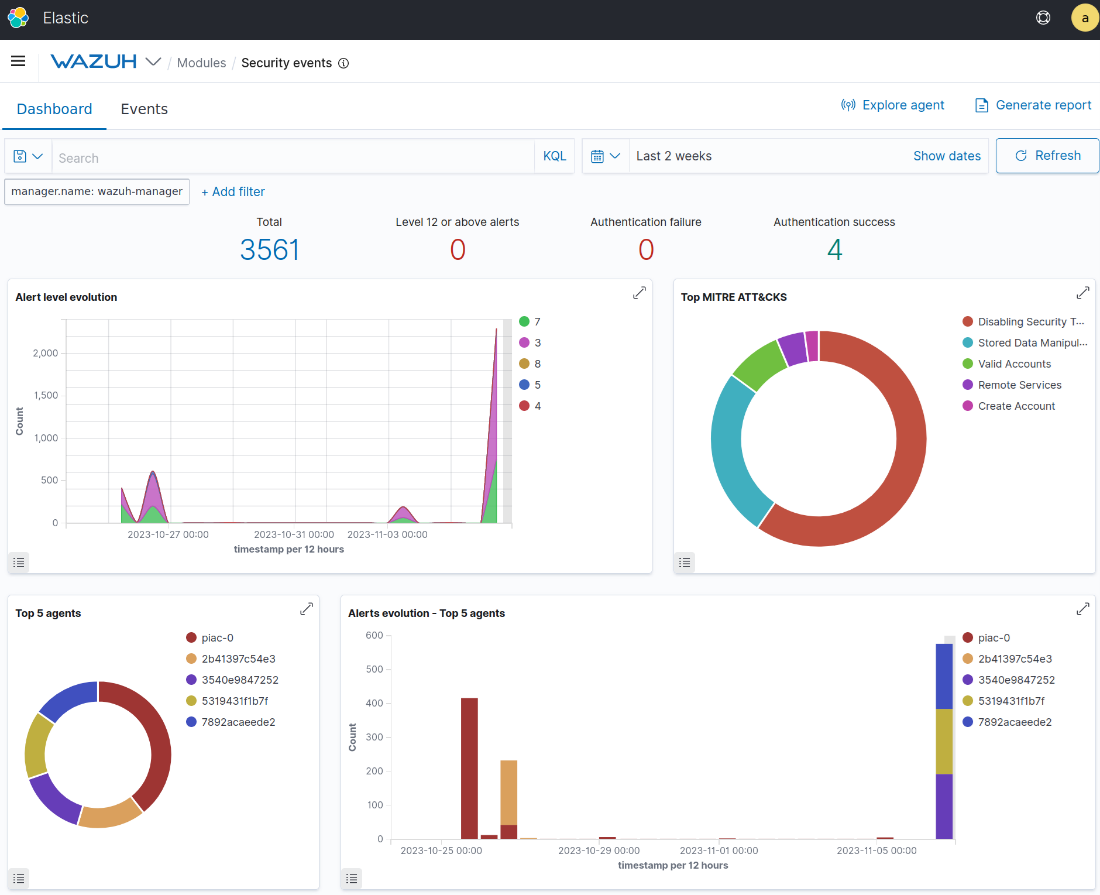
Figure 1: Wazuh SIEM is part of the Security Monitoring stack. It shows events stemming from different agents on infrastructure.
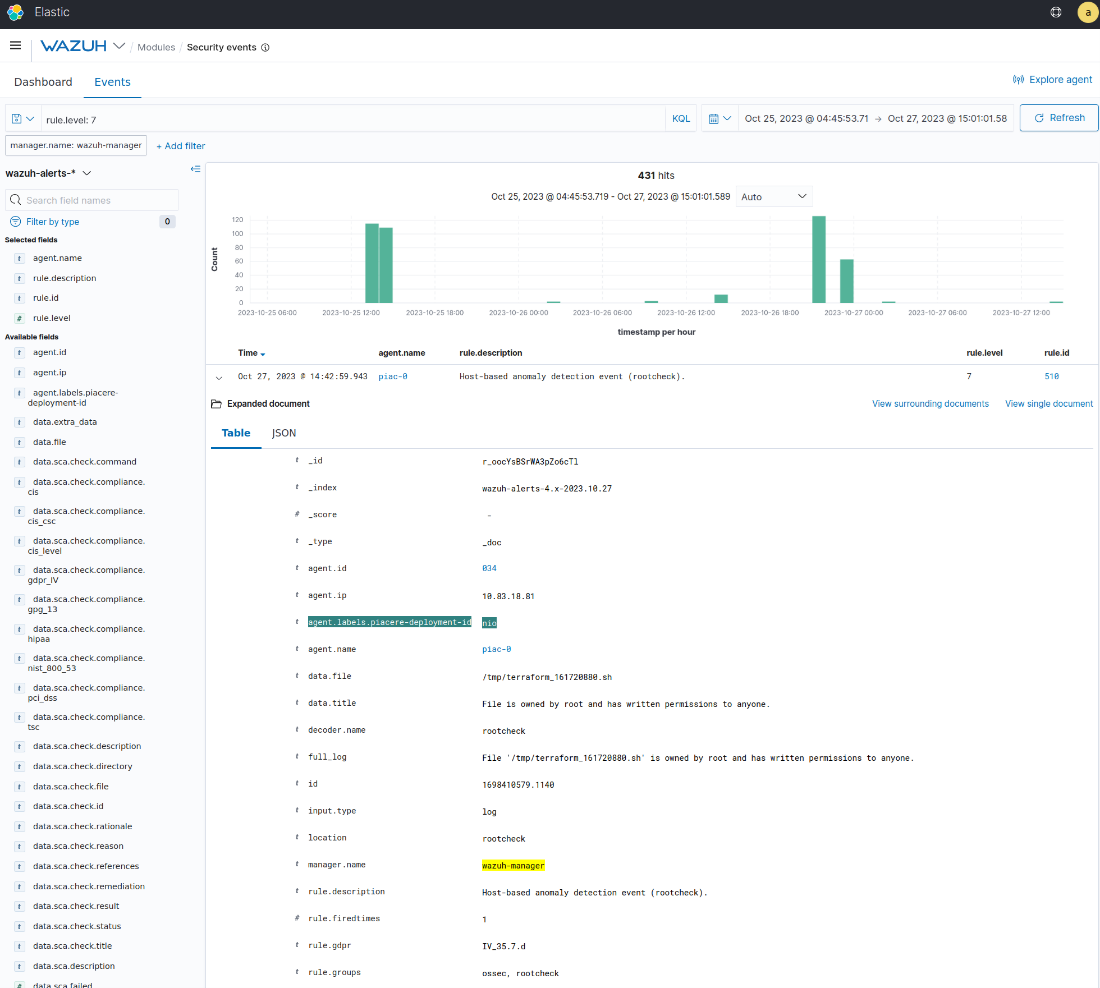
Figure 2: Specific PIACERE attributes are attached to the events. 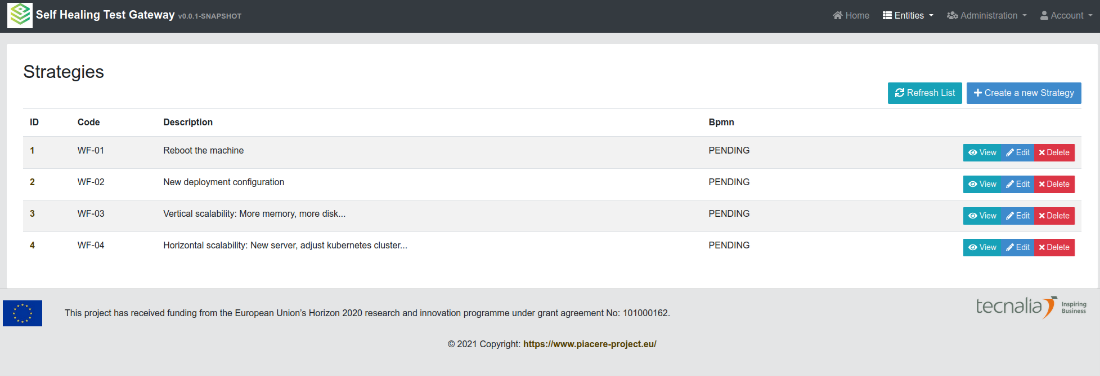
Figure 3: Self-Healing actions can be triggered as a result of the specific severity of security events.
PIACERE at runtime is able to automatically deploy security monitoring agents, integrated into the monitoring mechanisms and notify about security threats according to the policies, defined in the NFRs in the DOML language; allowing for self-learning and self-healing, and tackle unexpected situations that may affect the correct performance of IaC and its underlying environment (i.e. infrastructure security/compliance issues, infrastructure failures, deterioration in the response time, etc.).
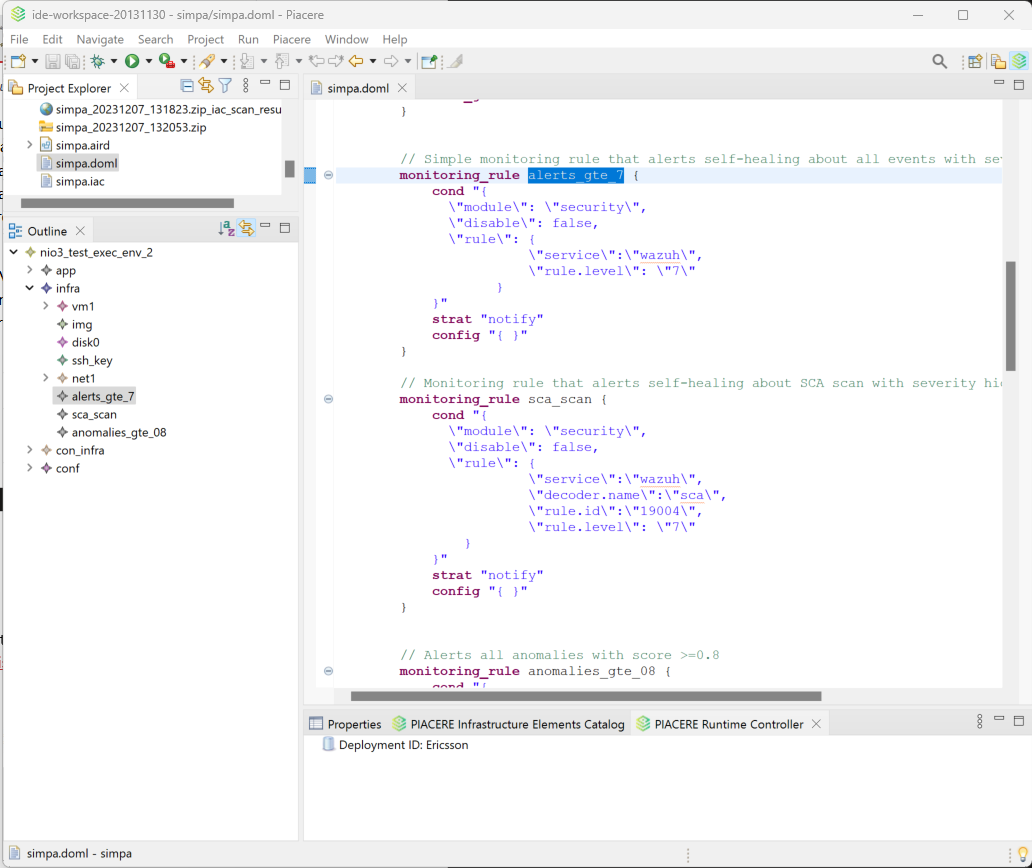
Figure 4: Expressing security monitoring rules in DOML language in the PIACERE IDE.
In the current stage we can express simple NFRs in DOML defining automatic self-healing actions that are capable of simple mitigation steps, e.g., triggering more diverse actions based on the detected security issue. In the next steps we shall extend type of supported strategies which currently support real time notifications to the users with more specific mitigation strategies (e.g., executing patches,, Ansible playbooks), depending on the identified security issue.

0 Comments