In this month of June we are concluding the second couching programme by the European Commission initiative Horizon Results Booster in collaboration with the META Group. It concluded 6 sessions to define and analyse three Key Exploitable Results across two consecutive coaching seminars. In the first one held in the Q4 of 2021, dedicated to the exploitation strategy, the consortium was guided by the experts through the definition of the project’s Key Exploitable Results, their use options, risk assessment and exploitation roadmap. A first report was generated to feed the first report on exploitation activities in the confidential deliverable D8.5. The second seminar focused the business plan development, through the appropriate definition of the Lean Canvas and the Value Proposition Canvas business tools that greatly improved the business intelligence in the project.
The first coaching programme by the European initiative Horizon Results Booster (HRB), named Exploitation Strategy Seminar (ESS) had the objective to guide brainstorming sessions on the use of the project’s results. It helped the team to characterise a selection of these results, identify the risks and potential obstacles for their exploitation, and analyse how to better address them in the context of their nature and of the nature of the key beneficiaries holding their IP ownership. A first meeting was held in 16.12.2021 dedicated to the introduction to the participants and content of the programme, and to the essential knowledge to better perform Communication, Dissemination and Exploitation. It was followed by several interactions with the HRB mentors and hands-on workshops where three selected key results were described and discussed, originating the ESS final report.
In this exploitation effort, we have focused on elaborating on the Key Results (KRs) of the project in the sense of what are the problems they are trying to solve, how is the proposed technology addressing those problems, and what is the unique value proposition (UVP) that will determine the differentiator of the solution that will derive from them. These KRs represent the innovation assets, offered by the PIACERE project to the open source and the scientific communities, and through their exploitation, to the European business ecosystem. They are distributed across three Key Exploitable Results addressing the Development [DEV], the Security [SEC] and the Operations [OPS], based on the KR innovation assets that they include and are built from (see Figure 1). Their exploration was prepared in the context of the Horizon Results Booster European Commission initiative, and the results of that data collection and analysis are available to the consortium through a live and actionable document in the project’s repository that can serve as guidance for the further technical work. It includes the planned “market watch” aiming to keep the project in sync with the market and scientific landscapes.
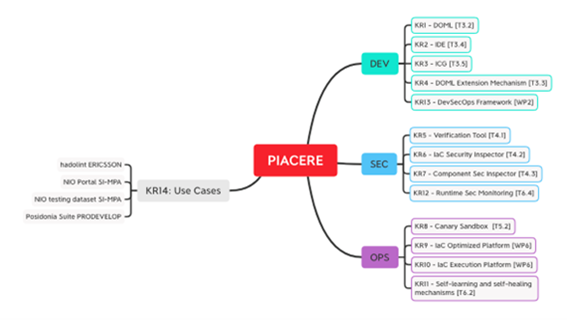
Figure 1 – Distribution of Key Results through PIACERE’s KERs
Having in mind, that the time dedicated to the ESS seminar allows only for a few results to be discussed, we shall take the lessons learned and provide the base for further developing of this exploitation analysis for all the other KRs. Moreover, during Q1 of 2022 the consortium, building on the ESS work, followed through a new coaching programme dedicated to the Business Plan Development focusing the KER 10, i. e., the IaC Execution Manager. This KER was identified as in the ESS analysis as the KER potentiating further exploitation work, and the gained know-how can be extended to the business model of the other KERs of the project. This HRB programme was held throughout April and May 2022, with a first webinar held in 22.4.2022 with the PIACERE consortium, and a hands-on workshop held in 20.5.2022 following the exchange of the supporting documentation guided by HRB templates. At the time of the writing of this blog post, PIACERE’s assigned workforce has been working to complement the final input according to the HRB expert recommendations, with the Value Proposition Canvas, to receive the final report in this month of June, proceeding then with the transfer of know-how to KR1 (DOML) and KR6 (ICSI).
DEV KER1: DevSecOps Modelling Language (DOML)
- Problem Addressed: To improve the ability of (non-)expert DevSecOps teams to model provisioning, deployment and configuration needs in complex contexts by providing a set of abstractions of execution environments and composing them into machine-readable representations.
- Solution Description: DOML is the end-user language enabling the modelling of deployment and configuration of complex infrastructural software in a way that can then be transformed by Infrastructure as Code Generator (ICG) in executable Infrastructure as Code (IaC).
- Unique Value Proposition: DOML language for expressing user-defined properties allows DevSecOps teams to select and combine the abstractions with the purpose of creating a proper infrastructure provisioning, configuration management, deployment and self-healing model.
@Horizon Results Platform: https://ec.europa.eu/info/funding-tenders/opportunities/portal/screen/opportunities/horizon-results-platform/44131
DEV KER2: IaC Code Security Inspector (ICSI)
- Problem Addressed: Lack of possibility to check the correctness of deployment scripts done by users, having very limited trust in the automated deployment systems (especially when approaching new users/customers that have no experience in automated or continuous deployment systems).
- Solution Description: This technology executes a series of checks over the particular IaC. On behalf of user, it also tracks all invocations per IaC project, enables sharing IaC projects among users and provides history (and potential recommendations) for each invocation.
- Unique Value Proposition: This tool will check the IaC code for errors and report back to the user with a set of error reports and also recommendations where inefficiencies are in his code. The integration of the verification tool will enable the customers to optimize and reduce the number of errors in their deployment procedure. This step in the deployment process can be fully automated and integrated into the deployment pipeline or done manually as a once off process for a selected part of the IaC code.
@Horizon Results Platform: https://ec.europa.eu/info/funding-tenders/opportunities/portal/screen/opportunities/horizon-results-platform/44193
OPS KER3: PIACERE OPS: IaC Execution Manager (IEM)
- Problem Addressed: Develop and maintain infrastructure as code for heterogeneous infrastructures and different phases (configure, provision, deploy, orchestrate), supporting multilingualism with one tool.
- Solution Description: Platform to automatically plan, prepare, and provision the infrastructure and plan, prepare, and install the software elements needed for the application to seamlessly run.
- Unique Value Proposition: Automatic, parametrizable, and therefore faster and easier execution, orchestration and deployment of IaC code on heterogeneous vendor providers, with no need to utilize different languages for the different providers, and it facilitates the exploitation of the project with independence to the provider.
@Horizon Results Platform: https://ec.europa.eu/info/funding-tenders/opportunities/portal/screen/opportunities/horizon-results-platform/44197
This will then be scaled to the applicability analysis of the project’s results in the context of the legal and regulatory landscape affecting the KERs, and the sustainability that will be investigated in the context of the exploitation potential of the achievements and the opportunities deriving from the use cases and the individual exploitation of project partners.
At the moment we have collected exploitation intentions from Consortium and characterized the exploitation of 3 KERs, defining their risk assessment and priority map. The described use options include: (i) consultancy/training on OSS; (ii) participation with IP results in other projects; (iii) Lean Canvas and Value Prop Canvas for IEM. Moreover we have described the exploitation roadmap in sync with the exploitation and communication strategy. Based on this knowledge we have profiled PIACERE in the Horizon Results Platform, will enrich the KER page on our website, and will soon profile the SEC technologies in the Cyberwatching.eu Marketplace.
In the next phase we are proceeding with the further analysis of other KRs, continuing the development of KER-focused business models, based on the appropriate protection of IP results and innovations.

0 Comments