With the increasing digital transformation across industries, in pair with the also fast increasing cybersecurity attacks of large impact, the need for a DevOps with security by design is essential. In the context of the innovative DevSecOps framework proposed by the PIACERE project, the security at design time considers: (i) the verification of the topological and architectural consistency of DOML deployment models; (ii) the inspection of the IaC code providing warnings about potential security issues of the IaC configuration and suggestions for possible corrections of the existing code; and (iii) a complementary inspection aiming to identify used components and problematic dependencies, extending the Ansible scanner IP background. While (i) is to be discussed in the context of DOML, the tools described at (ii) and (iii) will be the focus of this blog post.
IaC security inspection at design time is provided at PIACERE by a suite of static analysis and model checking tools aiming at supporting verification of correctness, safety, performance and data transfer privacy of all application components a monitoring system, capable of detecting security-related events and incidents in the deployed application’s environment. The monitoring system is deployable automatically and notifies users about security alerts. We apply static analysis to both the abstract model and the related infrastructural code, to execute and verify any security violation at runtime.
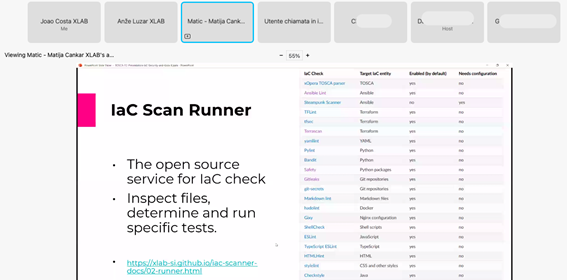
Fig1 – Presentation of the PIACERE technology to the TOSCA Community at their yearly meeting by Matija Cankar and Anže Luzar (XLAB)
Some are security checks and some others are component checks, technically the process to envoke them is similar but the aims are different. The security check identifies problems in the IaC code, including (but not limited to) typos, flows, undefined or wrongly defined, wrong ports open. On the other hand, the component check is checking how secure is the usage of components we rely on, and that need to be up to date, properly used and properly configured (the collection needs to be checked). This technology is available open source at GitHub and fully documented at GitLab.
The PIACERE team has been busy creating some momentum to its tools and methodologies, also highlighting the security mechanisms like the IaC security inspection as well as the component inspection, next to impactful communities as the GAIA-X (with whom XLAB is collaborating with in the context of cloud orchestration), TOSCA (in which XLAB has been an active participant and is eager to identify opportunities in PIACERE even though the TOSCA-independent approach), and the overall scientific community (through consistent iterations through events like, e.g., TELFOR 2022 and papers as [1] and [2]).

Fig2 – Presentation of the PIACERE research achievements to the Scientific Community at TELFOR 2022 by Nenad Petrović (XLAB)
The business unit of XLAB has also been busy leveraging the opportunities that arise from some of the premium features that are being developed to complement the already rich OSS functionality of the IaC security inspection. While most part of the scans provided by PIACERE’s IaC Security Inspector are freely available others are offered as paid premium features. One of them is XLAB’s owned Ansible playbook scanner – released in the end of October at the Ansible Fest 2022 as Steampunk SPOTTER – that inspects Ansible playbooks and returns warnings and recommendations, allowing to improve the quality of those playbooks and to get an instant quality score with tips on how to improve them.

Fig3 – Presentation of SPOTTER to the Ansible Community at Ansible Fest 2022 by Gregor Berginc and Matej Artač (XLAB)
References:
[1] J. Alonso, R. Piliszek, M. Cankar (2022). Embracing IaC through the DevSecOps philosophy: Concepts, challenges, and a reference framework. IEEE Software. DOI: 10.1109/MS.2022.3212194
[2] N. Petrović, M. Cankar, A. Luzar (2022) Automated Approach to IaC Code Inspection Using Python-Based DevSecOps Tool. To be published in the proceedings of the 30th TELFOR conference

0 Comments