Public Safety on IoT in 5G
This validation scenario will solve the following issues:
Mobile networks are well-suited for these kinds of public safety applications because of their ability to handle traffic from large numbers of low-energy devices that are transmitting small volumes of data. Massive IoT can be used to save lives through disaster monitoring and early warnings.
So those critical functionalities must be design and developed with the highest possible security policies so that it is mandatory to adopt an approach which can guarantee a security by design.
Moreover, given the modern incremental development process (DevOps), those security by design principles needs to be dynamically ensured and integrated in the SW development pipeline.
Adopting DevSecOps the above considerations will be well taken into account.
Application where PIACERE will be used:
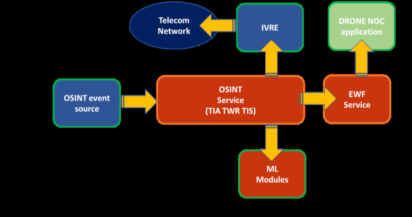
Emergency Warning Function Service Public Safety on IoT in 5G are emerging services in order to:
• Providing stable, secure, and future-proof mobile broadband services.
• To have the latest communications systems as well as a cost-effective way to add new digital broadband services, such as HD video for real-time situational awareness, mobile positioning and cellular Internet of Things (IoT), including asset management and connected logistics solutions.
• Dispatch the best-suited response teams.
Using the PIACERE platform will provide a way to verify benefits of the DevSecOps approach for designing and implementing the “public safety application”.
Expected benefits/ improvements using PIACERE tools
• It will ensure to adopt the DevSecOps approach, in order to proof its benefits on development of sensitive and critical infrastructure.
• It will guarantee improvements in terms of the quality, security and evolvability of infrastructural code, and enabling the reuse of pre-existing infrastructure-as-code approach in different contexts.
• It will provide feedback in exploring the security by design approach in the context of IoT distributed architectures and relevant technologies the goal to provide guidelines, principles and suggest frameworks to obtain provable security in the different layers of the products.